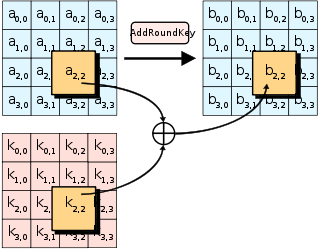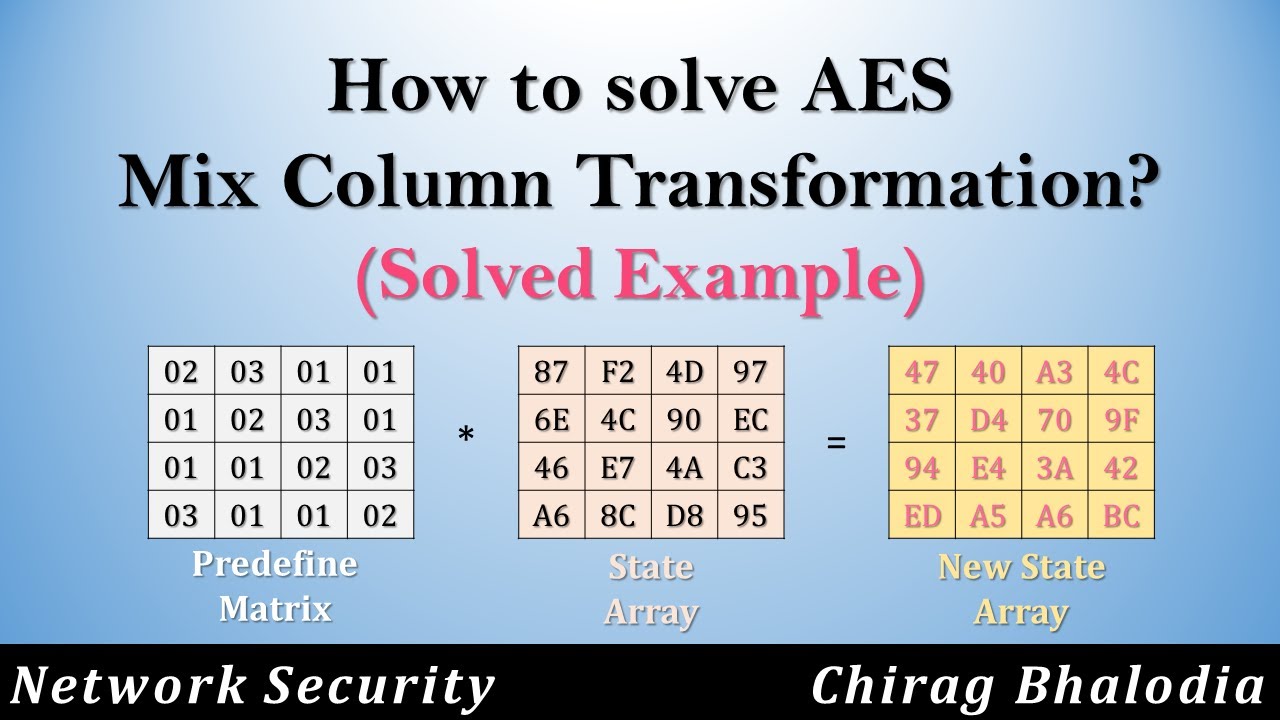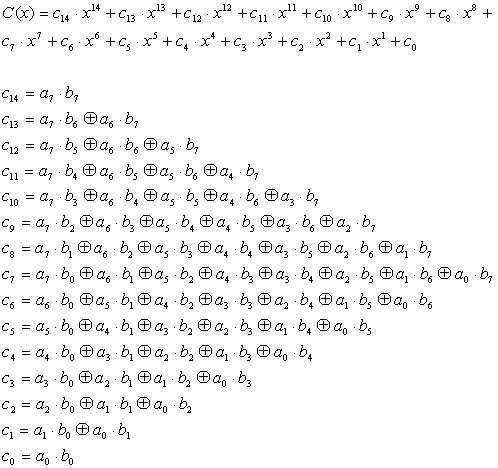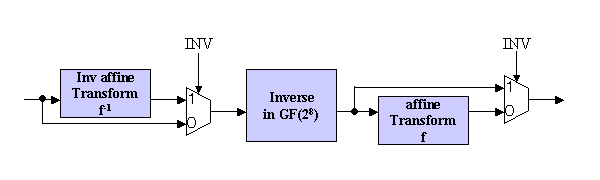
Symmetry | Free Full-Text | Modified Advanced Encryption Standard Algorithm for Information Security
![PDF] Implementing AES Encryption on Programmable Switches via Scrambled Lookup Tables | Semantic Scholar PDF] Implementing AES Encryption on Programmable Switches via Scrambled Lookup Tables | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e81407dd221afd6c1533ef2e688e83c096c1a78f/3-Figure1-1.png)
PDF] Implementing AES Encryption on Programmable Switches via Scrambled Lookup Tables | Semantic Scholar
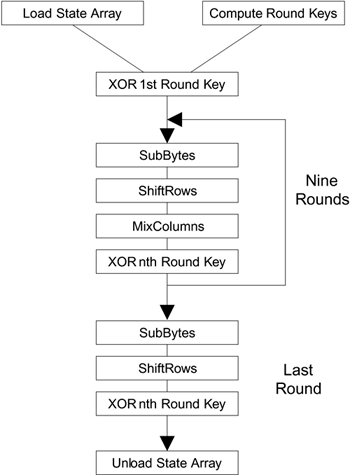
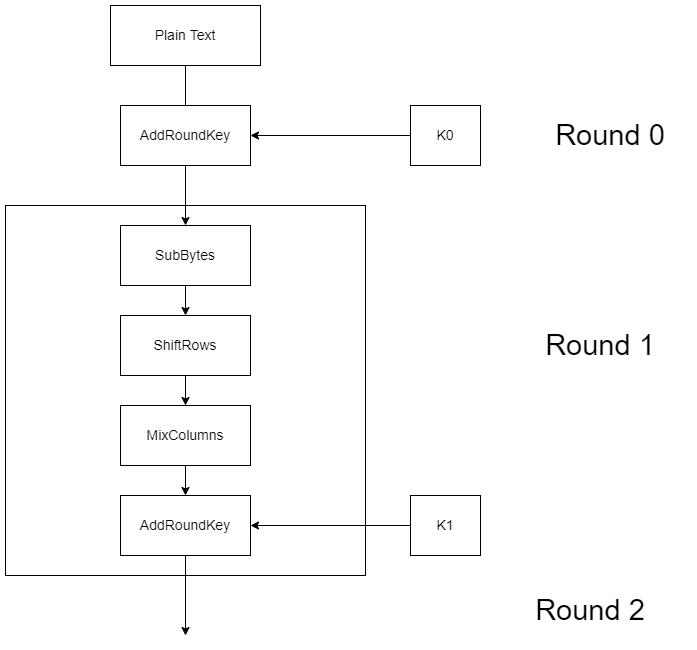
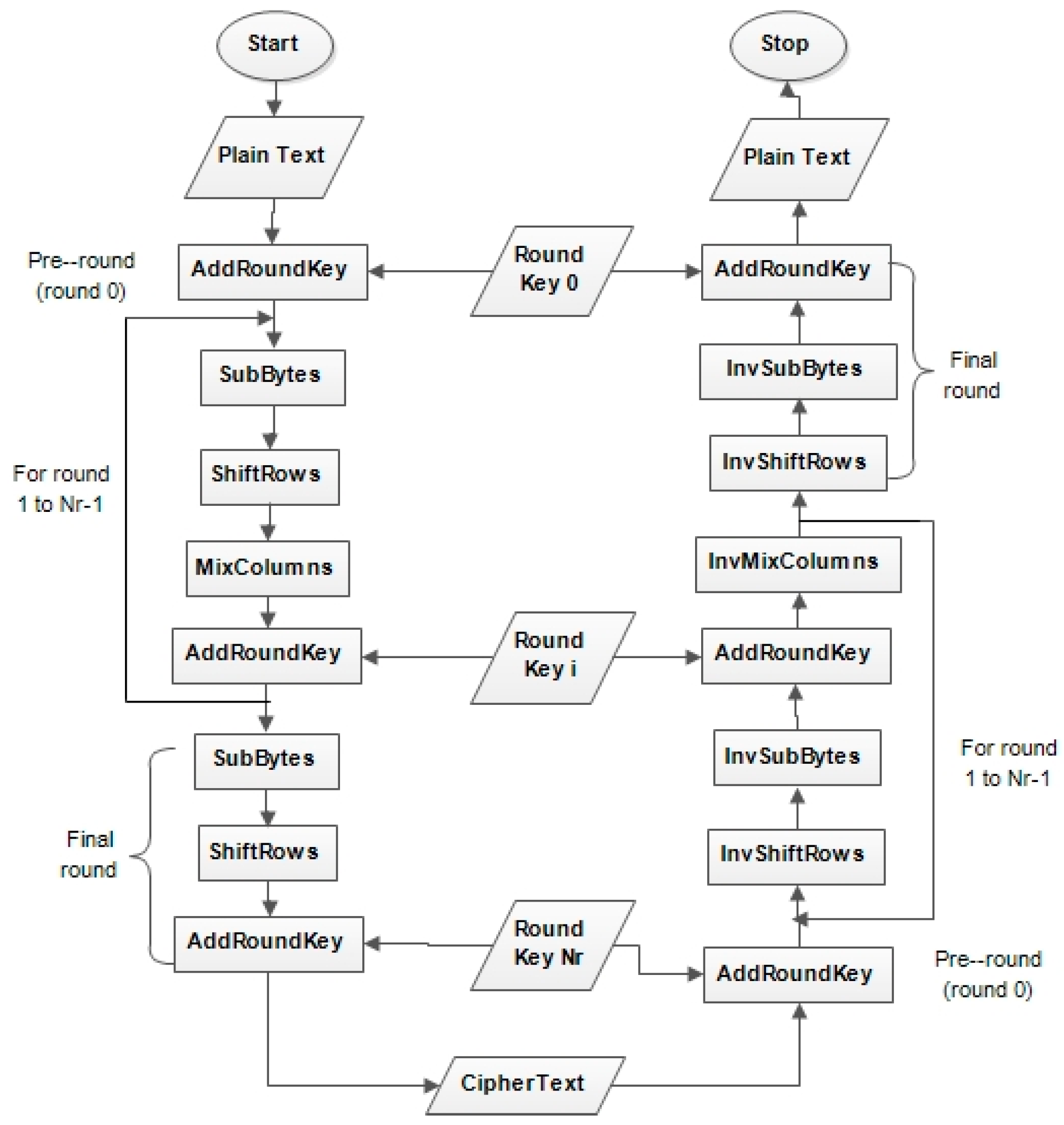
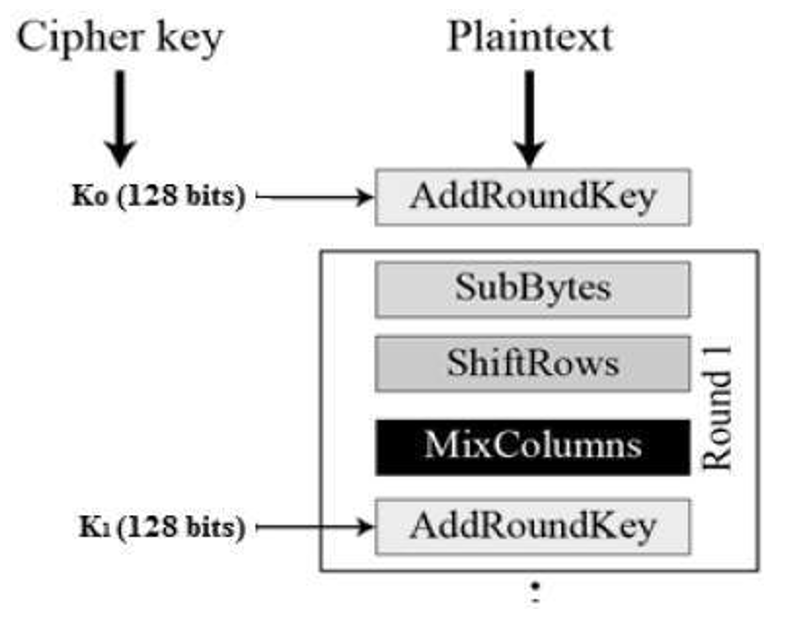
Steps in the AES Encryption Process :: Appendix A. Overview of the AES Block Cipher :: Appendixes :: 802.11 security. wi-fi protected access and 802.11i :: Networking :: eTutorials.org
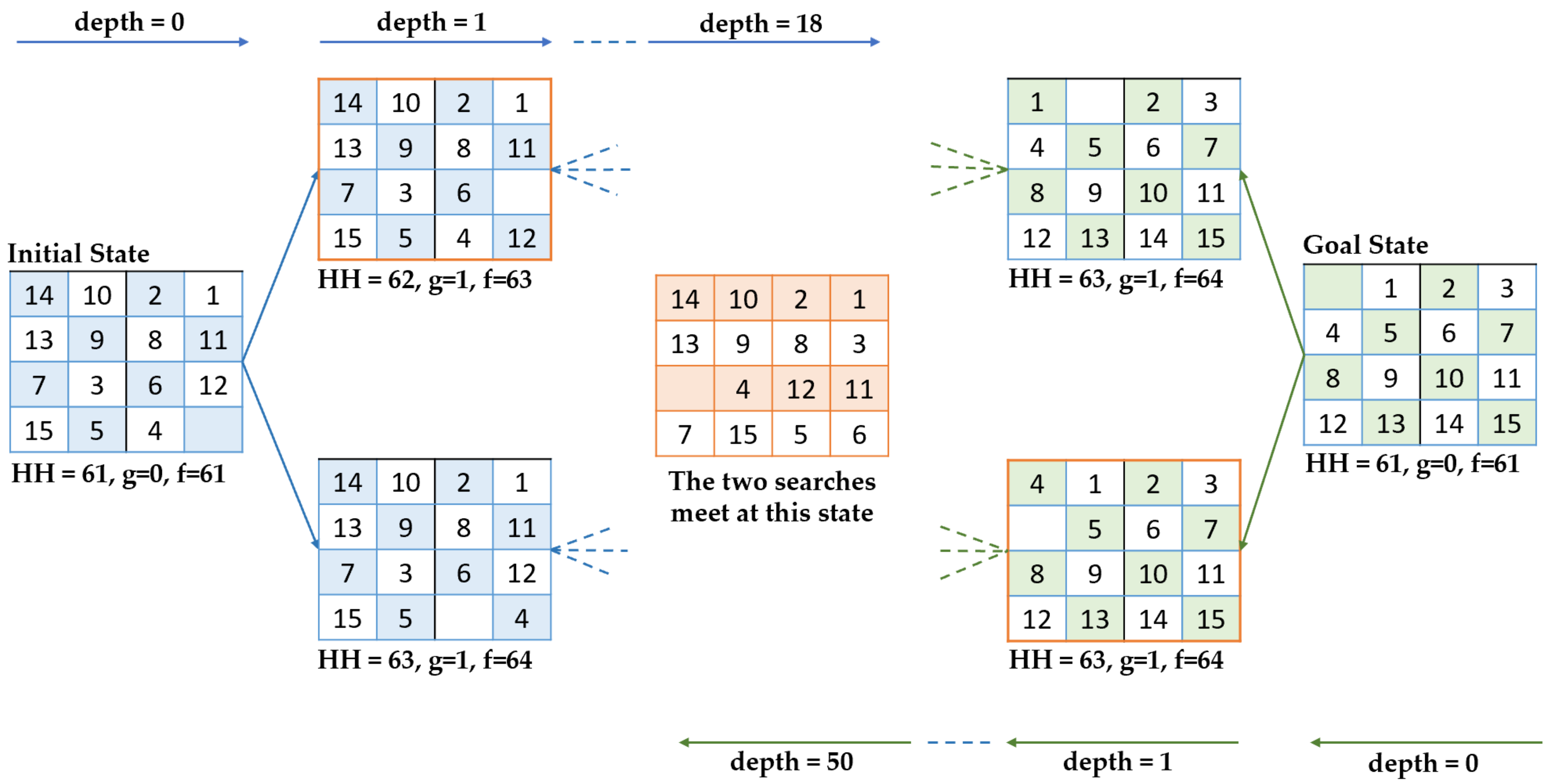
Computers | Free Full-Text | The Fifteen Puzzle—A New Approach through Hybridizing Three Heuristics Methods


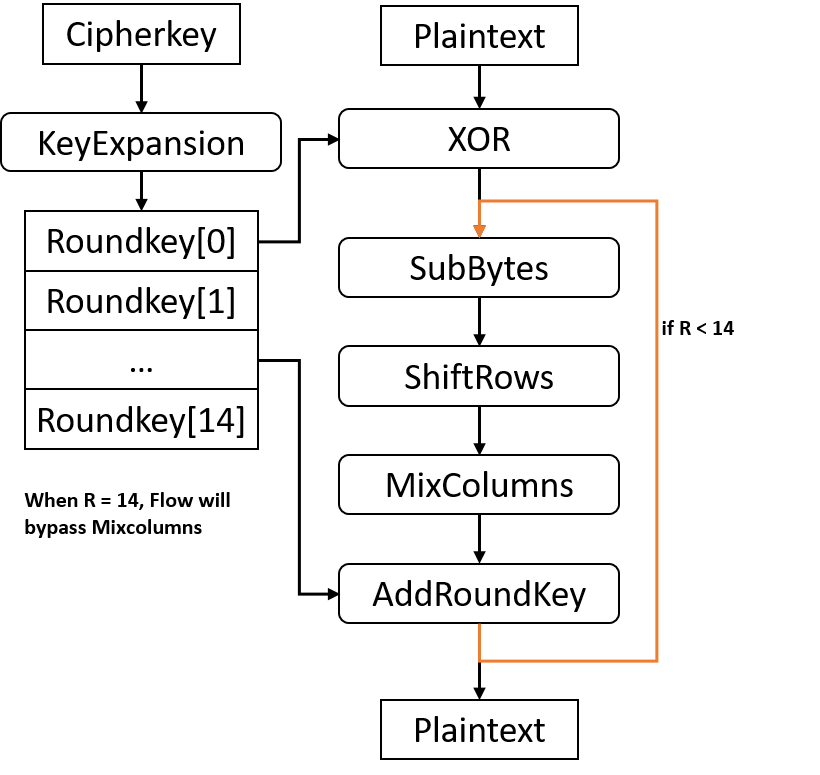
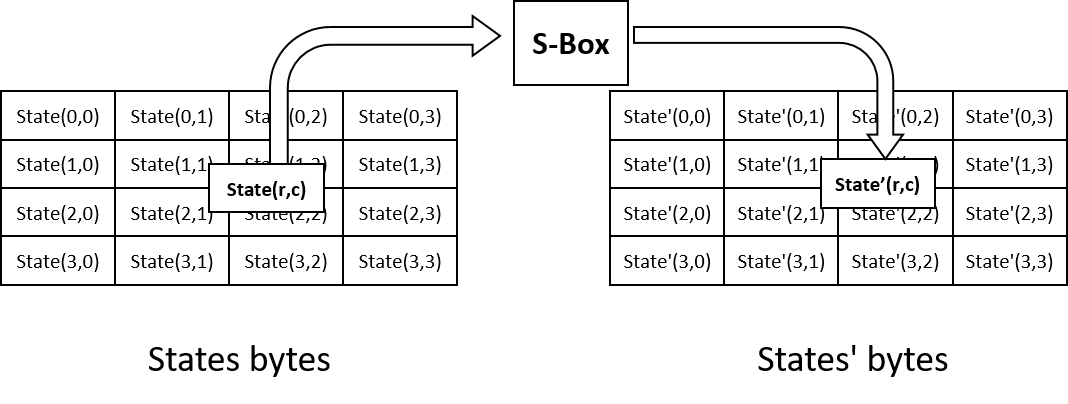
![SubBytes Stage in the traditional AES operation [25]. | Download Scientific Diagram SubBytes Stage in the traditional AES operation [25]. | Download Scientific Diagram](https://www.researchgate.net/publication/349016516/figure/fig1/AS:987363857682432@1612417296441/SubBytes-Stage-in-the-traditional-AES-operation-25.png)